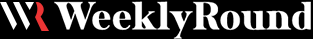10 Cybersecurity Tips Everyone Should Follow
The digital landscape is increasingly filled with sophisticated threats, making online safety more critical than ever. Cybercriminals target individuals and organizations alike, exploiting weak security practices to steal data and invade privacy. Following essential cybersecurity tips can help protect your personal information, finances, and digital reputation. Staying vigilant and informed is key to minimizing risks. For a closer look at the latest threats, visit the Cybersecurity & Infrastructure Security Agency and National Cyber Security Centre.
1. Use Strong, Unique Passwords

Creating strong, unique passwords for every account is a fundamental step in safeguarding your digital identity. Weak or reused passwords are easy targets for cybercriminals, making it crucial to use complex combinations of letters, numbers, and symbols. Avoid common words, personal information, or easily guessed patterns.
The NIST guidelines recommend long passphrases—at least 12 characters—for enhanced security. Consider using a reputable password manager to keep track of unique credentials for each account, reducing the temptation to recycle passwords and making your online presence much more secure.
2. Enable Two-Factor Authentication

Two-factor authentication (2FA) significantly boosts your account security by requiring an additional verification step beyond your password. This extra layer can include a text message code, authentication app, or biometric methods like fingerprints.
Even if a password is compromised, 2FA makes unauthorized access much more difficult. Always enable 2FA on your most sensitive accounts, such as email, banking, and social media. For more information on how 2FA works and why it’s effective, visit the CISA guide on strong authentication.
3. Keep Software Up to Date

Outdated software is a common gateway for cybercriminals to exploit vulnerabilities and gain unauthorized access to your devices. Regularly updating your operating system, browsers, and applications ensures that you receive the latest security patches and bug fixes.
High-profile breaches, such as the 2017 Equifax incident, occurred due to unpatched software vulnerabilities. Set your devices to update automatically whenever possible to minimize risk. For more information on the importance of software updates, visit the CISA patching basics page.
4. Be Wary of Phishing Scams
Phishing scams use deceptive emails, messages, or websites to trick you into revealing sensitive information like passwords or financial details. Common tactics include urgent requests, spoofed sender addresses, and links to fake login pages.
Always scrutinize unexpected messages, especially those asking for personal information or containing attachments. If you suspect a phishing attempt, do not click any links and report the message to your IT department or email provider. For detailed advice on identifying and avoiding phishing, consult the Federal Trade Commission’s phishing guide.
5. Protect Your Personal Information Online
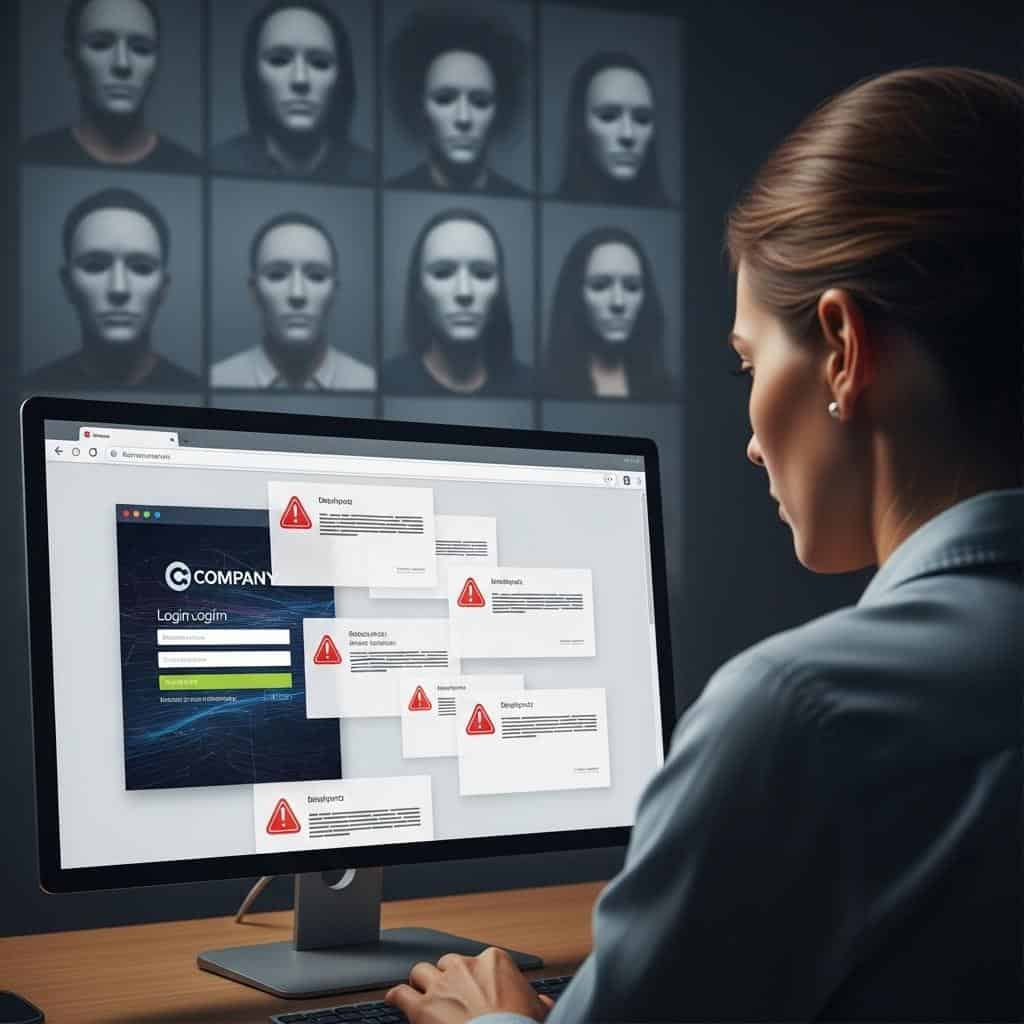
Be cautious about the personal details you share on social media and online forms. Oversharing information like your birthdate, address, or even pet names can make it easier for cybercriminals to commit identity theft or social engineering attacks.
Adjust your privacy settings to limit access to your posts, and only provide necessary details when filling out online forms. Think twice before posting sensitive information publicly. For more strategies on safeguarding your identity, review the recommendations from the Identity Theft Resource Center.
6. Use Secure Wi-Fi Connections

Public Wi-Fi networks are often unsecured, making it easy for hackers to intercept your data. Avoid accessing sensitive accounts or making online purchases on public networks. At home, secure your Wi-Fi with a strong, unique password and enable WPA3 or WPA2 encryption to prevent unauthorized access. Using a virtual private network (VPN) adds an extra layer of protection by encrypting your internet traffic. For more tips on securing your wireless network, check out the FCC’s guide to wireless network security.
7. Back Up Your Data Regularly

Regular data backups are essential for protecting your important files from ransomware, malware, or hardware failures. By keeping up-to-date copies of your data, you can quickly recover lost information in the event of an incident.
Use a combination of external hard drives and cloud storage for redundancy. Schedule automatic backups to ensure consistency and reduce the risk of forgetting. For detailed guidance on effective backup strategies, consult the National Cyber Security Centre’s backup advice, which outlines best practices for both individuals and organizations.
8. Install and Update Antivirus Software

Antivirus software is a key defense against malware, viruses, ransomware, and other online threats. It scans your system for malicious files and blocks suspicious activity before it can do harm. Keeping your antivirus software updated ensures it can recognize and respond to the latest threats.
Popular solutions like Norton, Bitdefender, and Kaspersky offer comprehensive protection, while free options like Avast provide basic security. Regularly review your antivirus settings and schedules for automatic updates. For unbiased comparisons and recommendations, visit Consumer Reports’ antivirus software guide.
9. Monitor Account Activity
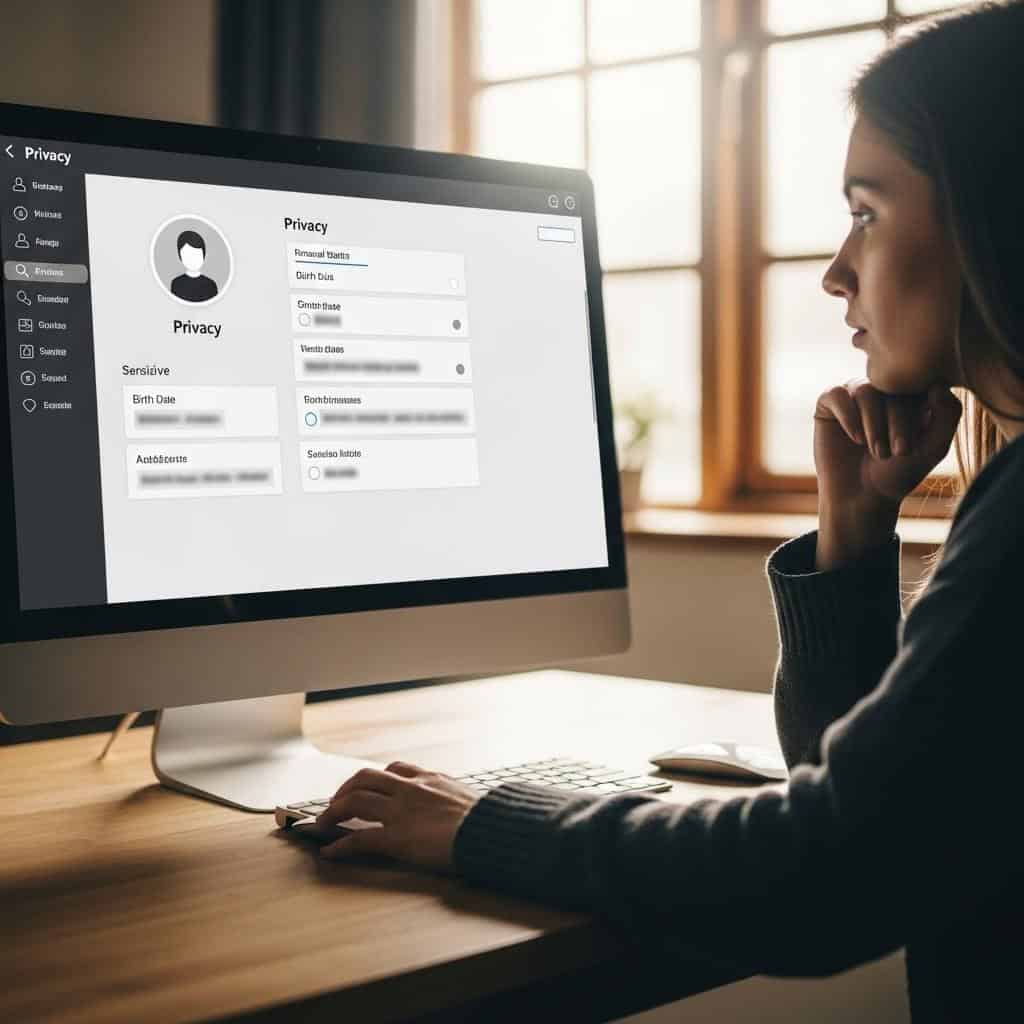
Regularly reviewing your bank, email, and social media accounts for unusual activity is vital to catching unauthorized access early. Look for unfamiliar logins, password changes, or unrecognized transactions. Most platforms allow you to enable alerts for suspicious activity, login attempts, or large withdrawals.
Reviewing your account logs helps you quickly spot and respond to potential threats. For more details on monitoring your accounts and setting up alerts, refer to the Cybersecurity & Infrastructure Security Agency’s monitoring tips.
10. Educate Yourself About Cyber Threats

Staying updated on the latest cyber threats and scams empowers you to make safer online decisions. Cybercriminals constantly evolve their tactics, so ongoing education is crucial for recognizing new risks. Regularly read articles, attend webinars, or follow official cybersecurity organizations for trusted information.
Reputable sources like StaySafeOnline.org offer valuable resources, tips, and updates to help individuals and businesses stay protected. By making cybersecurity awareness a continuous habit, you’re better equipped to identify and avoid evolving digital dangers.
Conclusion

Adopting strong passwords, enabling two-factor authentication, keeping software updated, and staying alert for threats are all vital steps toward safer online experiences. Regular data backups, secure Wi-Fi, reliable antivirus software, and continuous education further boost your defenses.
By proactively following these best practices, you significantly reduce your risk of cybercrime and identity theft. Make these habits part of your daily routine for lasting digital security. For more practical guidance and ongoing tips, visit resources like StaySafeOnline.org and CISA.